
Ransomware Attacks, Types, Prevention & Protection
Ransomware Attacks has a meteoric rise to being considered one of the major threats to…

Ransomware Attacks has a meteoric rise to being considered one of the major threats to cybersecurity in modern-day life. Whether you are an individual simply browsing the internet or an organization handling sensitive data, ransomware poses imminent threats to all. This guide looks at everything you need to know, ranging from its origin to types…

In 2025, the digital landscape is more connected than ever before. While this connectivity brings convenience and innovation, it also exposes organizations to complex cybersecurity challenges. From sophisticated ransomware attacks to AI-powered threats, businesses and individuals must adopt advanced security frameworks to stay protected. This article explores the key cyber security threats, strategies, services, and…

The digital revolution has transformed interactions and transactions for enterprises and people alike; new concepts and new efficiencies have mushroomed. Technology dependence on the one hand naturally leads to some drawbacks like the risk of cyberattacks, data breaches, and exposure to system vulnerabilities. Heavy reliance on cybersecurity analysts protects organizations against these threats. If you…

Overview (What you’ll find on this page)In this guide, you will be taken stepwise through AI in blockchain, what blockchain and AI are, how artificial intelligence in blockchain works, actual blockchain AI use cases, the benefits of AI in blockchain, and the most significant AI blockchain future trends to know about. The target audience is…

Phishing has been the most persistent form of cybercrime for decades, but today, thanks to the infusion of artificial intelligence, it has received a new birth. Modern AI phishing attacks are more convincing, scalable, and much harder to pin down compared to the previous generation of scams. In fact, this evolution represents one of the…
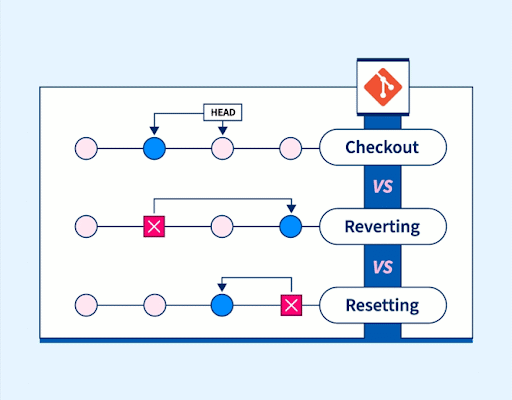
Even the best of developers can go wrong sometimes, but what makes them great is knowing undoing changes in Git quickly and safely. Committed wrong code, merged too soon, or accidentally edited the wrong file, and suddenly, you feel lost and stuck. Git offers reset, revert, and checkout to help. And in this article, you…
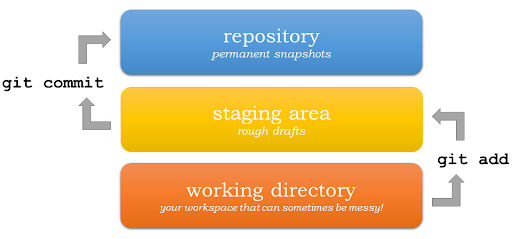
Introduction Those new to version control get befuddled by some terms; it gets worse when one encounters terms such as working directory in Git, staging area Git, and Git local repository. Once considered carefully, putting them together makes it much easier to use Git, which becomes a powerful tool and quite an intuitive one at…
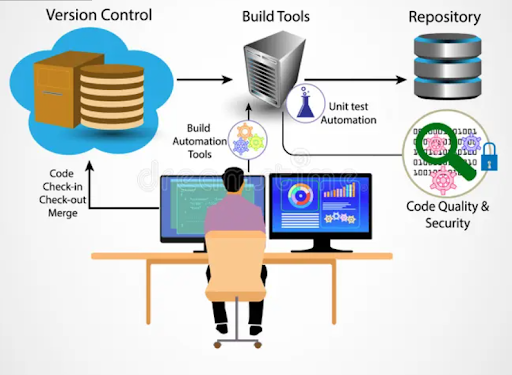
Introduction Tracking any code changes is crucial, whether you build websites or apps or any digital product. This is where source control systems come in. This beginner’s guide will take you through version control, why it is mandatory for developers, the types of version control systems, and popular tools like Git, the most widely used control…

What Is Git and Why Should You Learn It? In short, this is a version control system that monitors changes to files in your project. It makes it possible for developers to: If you ever worked on a Word document and saved such versions as “project_final_FINAL_2.docx,” you understand the issue this tool solves — organized…

Security is the primary concern when it comes to building modern backend applications. Whether a project is being worked on on the side or whether it is a full-fledged production app, endpoints must be blocked from unauthorized access. And that is why JWT authentication in Node.js will come in handy. In this article, we will…